Critical vulnerabilities found in Rockwell Factorytalk Assetcentre

The Claroty research team has disclosed nine vulnerabilities in Rockwell’s FactoryTalk AssetCentre, all of which were assigned the highest CVSS criticality score of 10.
ICS-CERT published an advisory (ICSA-21-091-01) that includes vulnerability and mitigation information, with users urged to update FactoryTalk Asset Centre to v11 or above immediately.
According to Claroty, Rockwell Automation’s FactoryTalk AssetCentre product sits centre stage in many industrial enterprises, overseeing backup and disaster recovery services, version and source control, and inventory management of automation assets.
These functions are designed to ensure continuity and uptime, two cornerstones of ICS networks. ICS-specific backup solutions such as FactoryTalk AssetCentre are key elements that enable quick disaster recovery in the event of, for example, a targeted ransomware attack.
In industries where downtime is unacceptable, and especially where public safety may be impacted, organisations must have a reliable backup available.
As part of its strategic research on these types of product lines, the Claroty Research Team focused on the pre-authentication attack surface of the FactoryTalk suite, specifically FactoryTalk AssetCentre. The company examined the ability of an attacker to compromise the backup server, own the ICS data, and have direct access to lower-level devices. These types of attacks can be devastating, given the ransomware and extortion climate, and attackers’ targeting of backups in such intrusions.
Claroty privately disclosed a number of serious vulnerabilities in the product to Rockwell Automation, some of which could be used alone or chained to remotely access and execute arbitrary code.
An attacker who is able to successfully exploit these vulnerabilities could do so without authentication and control the centralised FactoryTalk AssetCentre Server and Windows-based engineering stations communicating with the server.
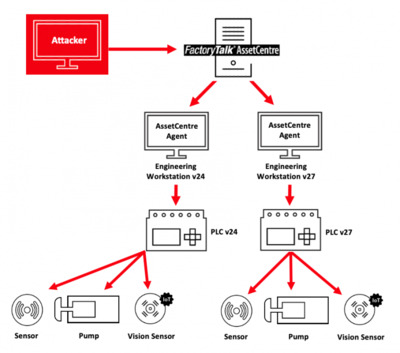
In short order, an attacker could own a facility’s entire operational technology (OT) network and run commands on server agents and automation devices such as programmable logic controllers (PLCs). This type of attack traverses the Purdue Model, from the operations level to the control level (see Figure).
All of the nine vulnerabilities were assessed a CVSS score of 10, the highest criticality score. Users are urged to update FactoryTalk Asset Centre to v11 or above, since FactoryTalk AssetCentre v10 and earlier versions are affected. ICS-CERT published the advisory on 1 April that includes vulnerability and mitigation information.
FactoryTalk AssetCentre a powerful target for attackers
FactoryTalk AssetCentre is a powerful, centralised tool where project files are stored for use on any Rockwell Automation platform. The AssetCentre architecture, from a high level, includes the main server, an MS-SQL server database, clients and remote agents.
The software agents run on engineering workstations (generally, Windows-based machines); the agents communicate with the centralised server and can accept and send commands to automation devices, such as PLCs. Project files are then updated and sent back to the server, which stores the files centrally. Operators can perform backup and restore, and version control functions from AssetCentre for all PLCs running on a factory floor, for example.
Claroty researchers were able to find deserialisation vulnerabilities in a number of remoting services running on FactoryTalk AssetCentre, which handle inter-process communication within an OT network, as well as SQL-injection vulnerabilities in other service functions. These services run with the highest system privileges, meaning that any arbitrary code supplied by an attacker would also execute with those same privileges, allowing full access to the machine.
Deserialisation vulnerabilities, meanwhile, are a class of bugs that occur when an attacker is able to inject malicious code into a serialised object that would be executed later when being deserialised. Programs such as FactoryTalk AssetCentre have many complex objects, representing different components in the system. As these objects are sent over the network to other instances of the software — AssetCentre in this case — they must be first serialised to binary data in order to be transferred and later deserialised back to a living object in the memory. Deserialisation vulnerabilities force targets to deserialise untrusted data and execute it; the impact of the attack would depend on the particular vulnerability.
Mitigations and recommendations
Rockwell Automation urges users to update FactoryTalk AssetCentre to v11 in order to mitigate these nine vulnerabilities. The company also recommends users refer to the FactoryTalk AssetCentre Installation Guide and follow guidance there in order to securely configure the tool with SSL on clients, agent computers and the web client.
Rockwell also recommends configuring IPSec for secure communication; however, the company acknowledges this does not completely address these vulnerabilities. While it would allow the system to authenticate senders and prevent unauthorised connections, an attacker that was able to leverage an authorised client would still be able to compromise the system. According to Rockwell, using IPSec reduces risk by reducing the potential attack surface.
The vulnerabilities
A more detailed description of the nine vulnerabilities can be found on the US CERT site.
Cyber attacks on water and electricity operators on the rise: study
A study has revealed that 62% of US and UK water and electricity operators were targeted by...
Orro launches asset discovery service for OT
Australian IT solutions provider Orro has announced it is offering its Digital Asset Discovery...
Rockwell launches factory-scale digital twin technology
Rockwell Automation has launched its Emulate3D Factory Test digital twin software at NVIDIA GTC...








