Understanding firewall technology for industrial cybersecurity — Part 1
By Dr Tobias Heer, Dr Oliver Kleineberg and Divij Agarwal, Belden*
Wednesday, 29 June, 2022

Firewalls are essential components for ensuring network security and increasing system robustness and resiliency.
Firewalls represent an indispensable tool for network security. As industrial systems have adopted Ethernet infrastructure and become interconnected to corporate IT systems, firewalls have become essential components for ensuring network security and increasing system robustness and resiliency. Rather than being a one-size-fits-all device, firewalls come in a variety of form factors with a range of features and technologies optimised to play different roles as part of a comprehensive security architecture.
An essential component of industrial network security
Modern security models adopt a holistic approach, taking into consideration not only technology but also the processes and people involved. This is why it has been a long time since firewalls alone have been promoted as a sufficient or exclusive measure for securing industrial plants and networks. Firewalls are, however, the core elements in network segmentation and therefore are an essential part of any network security strategy.1
Over time, the term ‘firewall’ has come to be very widely used and now applies to a broad range of technologies with different methods of operation and objectives. Today, the diverse firewall array includes: stateless and stateful firewalls, transparent firewalls, firewalls at various levels of the network reference architectures, firewalls with deep packet inspection and even firewalls with intrusion detection features. Then there are additional methods that can control and limit network traffic, such as access control lists. This leaves the system designer with the question of which type of firewall is appropriate for which use case.
General function of a firewall
Firewalls are devices that protect networks or network devices, such as industrial PCs, control systems, cameras and other devices from unauthorised access by preventing network traffic to or from these systems. The first broad distinction here is the difference between host firewalls and network firewalls. The first is installed on a computer (host) or already provided by the operating system as a software feature. Examples of these personal firewalls are the Windows system firewall or the iptables firewall, which is part of most Linux systems.
In contrast to that, network firewalls are specifically developed for use as a firewall and are placed in the network rather than on a PC. These network, or hardware, firewalls are important elements in industrial facilities, especially when they are connected to additional networks (such as office networks) or when wired transmissions are combined with wireless technologies. In these situations, a network firewall serves to establish the network boundary as the first line of defence against attacks and only allows desired traffic into and out of the network.
The fundamental technical function of any firewall is to filter packets. The firewall inspects each packet it receives to determine whether the packet corresponds to a desired template for traffic patterns. The firewall then filters (drops or discards) or forwards packets that match these templates. These templates are modelled in the form of rules. A firewall at the boundary of a network can, for example, include rules in the form of “A communication link within the network can only take place with a specified server” or “Only the PCs for remote maintenance can be reached outside the network, not any other devices.” A firewall protecting an operational zone of a plant floor might contain rules for industrial protocols, eg, Modbus/TCP, such as “Write commands for the Modbus/TCP protocol, coil 56, are permitted only from the maintenance terminal.”
Because network-based firewalls are of great significance for industrial facilities, this article focuses on those alone. But where are these firewalls used in today’s security models?
Firewalls in an industrial environment: applications and requirements
Firewalls are important components in today’s security strategies. Different types of firewalls are used in various locations within the network to provide different types of protection as part of a defence in depth2 strategy. Firewalls can secure the link between a company network and the industrial network to protect against external hacker attacks. Other types of firewalls separate devices within a network from each other, or permit only specified communications between devices to protect not only against malicious attack but also against device or operator error. The concept of precisely limiting communication between participants in internal networks, as well as partitioning of various network areas from each other, is known as zones and conduits. Zones and conduits are a central component of the international standard IEC 62443 and a key component of a defence in depth security strategy.
Defence in depth is a strategy where multiple layers of defence are implemented, in contrast to just one defence mechanism, a single firewall, for example. The reason why defence in depth and zones and conduits go together so well is that key elements of both strategies complement each other.
On one hand, defence in depth hampers attacks against networks through a set of layered defences — an attacker must defeat multiple security levels, not just a single obstacle. On the other hand, partitioning a network into multiple communication zones and implementing a ‘need to communicate’ strategy according to zones and conduits implicitly adds additional defence layers — layers that add to the resilience of the network in the case that one of the areas is compromised by an attacker. In this case, only the partitioned area that the attacker has been able to reach is compromised; the remainder of the network is protected. And, because the bulk of cyber incidents are related to device failure, software error, human error or malware, zones and conduits increase system reliability and robustness by keeping incidents in one zone from spreading to another.
The strategies of defence in depth and zones and conduits are not new. If you look at castle construction from any culture, you will see that layers of security were built into the castle design — moats, multiple walls, turrets. Individual zones of the castle are separated from each other by controlled conduits — gates, drawbridges and iron bars — to contain attackers and make their movements more difficult.
In communication networks, the isolation of groups of networked devices into zones and conduits represents the gates. This procedure should be applied in combination with a stacked defence in depth since gates are useless without walls. In order to implement these best practices in communication networks, numerous firewalls are used at various locations in the network.
Firewalls at network boundaries
Firewalls play various roles in partitioning networks. Firewalls can be used to protect a company’s enterprise networks against threats from the outside. In this case, this overall protection is the domain of IT firewall solutions that are placed in a company’s data centre. Firewalls can also be used to protect networks from each other; for example, to separate a production network from the company’s enterprise network.

A firewall in a small cell or external site
Industrial firewalls with router functions are perfect for smaller external sites. This allows, for example, distribution stations or remote work sites to be connected to the rest of the company’s control infrastructure via a cellular network. The firewall controls the flow of network traffic out of and into the external site’s local network. Because such a firewall represents the border between the company’s own network (the external site) and an external network (a provider network or the internet), the firewall must possess full capabilities for packet filtering and filtering traffic between various networks (see Figure 1). Such a firewall is called an IP firewall since it processes Internet Protocol (IP) traffic. Because these firewalls are often installed very near the actual facility, industrial hardening must also be taken into consideration. Extended temperature ranges or approval for use in special areas (such as energy supply, hazardous location and transportation) are crucial.
Firewalls at the field level
It is rarely sufficient to protect only the external boundaries of the network against attackers. Many threats actually originate inside a network. Industry studies have shown that most cyber incidents are not due to intentional external attacks but from software or device failures and human error. In a networked control system, errors and mistakes can quickly propagate within the system unless proper design steps are undertaken to isolate and contain failures. Thus, an effective cybersecurity strategy is not just about security but is also an important component of ensuring the safety, resiliency and reliability of your system.
In this case, firewalls can contribute to the overall resiliency against unintentional errors by limiting communication between different zones of the local network (see Figure 2). This requires a firewall that is tailored to fit this particular use case. If communication from outside the facility is only supposed to be possible with a single device, the firewall should specifically permit this connection while it prevents other attempts at communication.
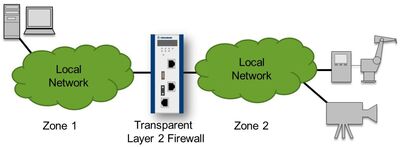
The demands put on a firewall in use within a network differ from the demands put on a firewall in use between networks. Therefore, a transparent Layer 2 firewall at the Ethernet level is required instead of an IP firewall. The key characteristic of a transparent Layer 2 firewall is shown in Figure 3. The Layer 2 firewall implements filtering functions on local communication, which usually happens on the Ethernet level or Layer 2 in the ISO-OSI layering model.
In contrast, pure Layer 3 firewalls are usually unaware of Layer 2 traffic. Therefore, the Layer 2 firewall is transparent to the upper protocol layers but performs a critical security function in local networks.
Due to the fact that these firewalls are usually implemented at the field level, the application parameters (temperature, vibration and other environmental factors), as well as the necessary approvals, must be taken into consideration. This results not only in significant functional differences of these devices, compared to conventional IT firewalls, but also in different outward appearance, device sizes, device housing, cooling (usually, only passive cooling is possible) as well as in supported network media and transceiver technology.

Firewalls in a WLAN
Communication from wireless to wired networks can also be controlled by firewalls. If a client is connected to a WLAN, it is possible, in principle, to communicate directly with all other devices in the same network. Thus, an attacker can extend a successful attack on a client that is connected to the WLAN to any other device on the Ethernet network.
This problem can be solved by restricting the forwarding of messages between WLAN clients with a firewall at the WLAN access point. For example, the communication of a tablet that is connected to a device via a WLAN can be limited so that it can only access data through the user interface but not additional subsystems or other devices connected to it.
In order to do this, the firewall must be implemented directly at the access point. Industrially hardened devices are important here as well.
In Part 2
In Part 2 of this article, we will examine in depth the different types of filtering available within industrial firewall devices and the ways in which multiple firewall devices can be best managed.
References
- National Institute of Standards and Technology NIST 2009, Guidelines on Firewalls and Firewall Policy, Revision 1.
- National Institute of Standards and Technology NIST 2011, Guide to Industrial Control Systems (ICS) Security.
IO-Link and the role of the IO-Link Master
While it is true that IO-Link is plug-and-play from a hardware perspective, it pays to do your...
Security enhanced for digitalised industrial boilers
Industrial boiler maker Bosch Industriekessel depends on secure gateway technology to offer...
Mineral processing: a eulogy for analog
Leading mines have already accomplished an automated, digitally connected mine and are reaping...